- System Log Mac Hacked Client Windows 10
- System Log Mac Hacked
- System Log Mac Hacked Download
- System Log Mac Hacked 2
- System Log Mac Hacked Client Windows
Feb 02, 2021 • Filed to: Solve Mac Problems • Proven solutions
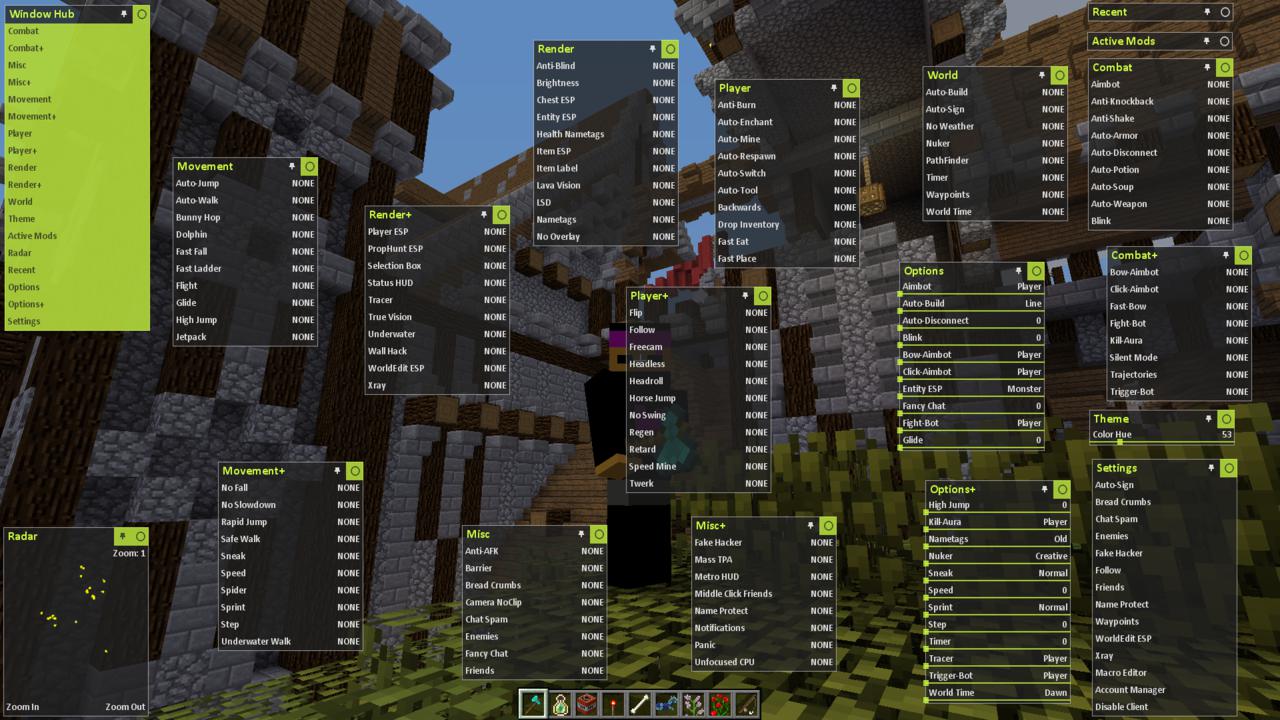
There could be situations when you need to hack your own Mac and situations when you have trouble remembering your login password. Do not freak out when this happens - it is not a big deal. Learning how to reset or bypass Mac OS X password will be a great advantage because not only are you able to have access back into your Mac, but also keep your Mac better protected as bypassing the login password is easy.
Part 1: How to Reset Login Password
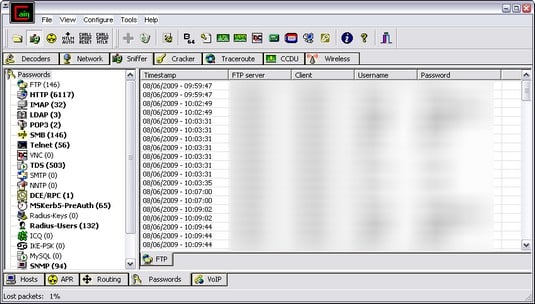
How to track down hacks with log files Any system can collect logs, but most security operations do a poor job of filtering them to find evidence of malicious activity. Apple replaced this traditional text system with the Unix text protocol with its new unified magazine in September 2016. This article can be found with a series of free browser browsers and other tools that, I believe, combine the power of the log-in with a much more accessible user interface.
As a good practice, we recommend refreshing your login password regularly. There are a couple of ways to do it.
Open the Apple menu located on the upper-right corner of the screen. Open 'System Preferences' and click on 'Users & Groups'.
Type in your username and password to 'Unlock' the Users & Groups preferences.
In the left panel, highlight your username. Click 'Reset Password'.
Key in your new password and verify it. For future reference, it is highly recommended that you place a hint. To finish the process, click the 'Change Password' button.
Part 2: How to Bypass Mac OS X Password
Now, while refreshing your password may be good practice, it is tiresome to remember your password. At one point or another, many of us just forget our passwords and there is no way for you to enter your account on your Mac.
Do not worry about that. Here are some ways you can bypass the Mac OS X password and regain access to your computer.
Method 1: Mac OS X installer CD
Pop in the Mac OS X installer CD and hold the 'C' button while you restart your Mac. Wait until the Apple logo and the 'Mac OS X Utilities' window appear. On the menu bar at the top of the screen, click 'Utilities'.
Click 'Terminal' and type 'resetpassword' in the prompt. Press the 'Enter' button on your keyboard.
Select the specific 'Volume Hard Drive' in the top section of the window. Select the 'User Account' that needs its password to be reset and enter the new password. Verify the password and click the 'Save' button.
Click 'OK' when the prompt asks you to verify your actions.
Once you get into your desktop, restart your Mac to boot it back to normal and log in using your new password.
Method Two: Reset the Password in Single User Mode
Not all of us keep the installer CD or know where we have kept it. Therefore, this method will come in handy. It will involve some command-line footwork, but do not let that scare you away.
Restart your Mac while holding the 'CMD' and 'S' buttons. Your Mac will boot itself into the Single User Mode.
Type the following commands and press 'Enter' on your keyboard after each line and wait until it prompts you to key in the next line.
If your Mac is running Snow Leopard or below, type the following and change username and new password accordingly:
If the Mac is running Lion or above, type the following commands instead, changing the username and new password accordingly:
You should now be able to access your Mac without restrictions.
Part 3: Protecting your Mac from Mac OS X Password Bypass
As you can see, it is really easy to hack into your own Mac. Therefore, you need to protect it from malicious intent. To add protection to your device, you can set up a firmware password. By having this layer of protection, an unauthorized third party will not be able to reset your machine even in single-user mode.
Here is how to go about it.
Pop in the Mac OS X Installer CD and wait for it to boot. You will soon be able to see the 'OS X 'Utilities' window.
Open the 'Utilities' menu and click 'Firmware Password Utility' to set a firmware password.
Check the checkbox, enter your firmware password and verify it. To apply the password, click 'OK'.
You can also add another layer of protection with 'FileVault'.
Open the 'Apple Menu' located on the upper right-hand corner of the screen. Open 'System Preferences' and click on 'Security & Privacy'.
Open the 'FileVault' tab and click 'Turn On FileVault'. Your disk is now encrypted.
As you can see, password recovery for Mac is easy to execute and usually does not take a long time to do - it is simple enough for you to save a trip to the Apple store. However, since it is uncomplicated to do, your Mac is vulnerable towards invasion. Therefore, it is important to know how to hack your own Mac and protect it from any unwanted attention!
System Log Mac Hacked Client Windows 10
What's Wrong with Mac
- Recover Your Mac
- Fix Your Mac
- Delete Your Mac
- Learn Mac Hacks
Short answer:
These are scams just like an unsolicited phone caller harassing you to buy something you don't want. You don't need to do anything but hang up and forget about it. Your phone cannot become infected simply by an unwanted call, right? Neither can your Mac. Do the equivalent of hanging up on the harassing phone caller: close the web page and forget about it. No other action is necessary, or justified.
Read Avoid phishing emails, fake 'virus' alerts, phony support calls, and other scams - Apple Support.
Long answer:
These popular browser scams spontaneously appear as an unexpected popup or unsolicited webpage (examples below; click to enlarge) that allege the detection of 'viruses' or the existence of some unsafe condition that needs to be addressed with great urgency:
Scam Example 1 | Scam Example 2 |
Scam Example 3 | Scam Example 4 |
Scam Example 5 | Scam Example 6 |
Scam Example 7 (iPhone) | Scam Example 8 (Apple Watch) |
These scams can appear on any web browser running on any Mac, PC, or iOS device.
Despite what they say your Mac has not been infected with anything other than a web page that won't go away, which is easy to fix. What gets people into trouble is believing the information that appears, and then taking inappropriate actions.
These scams may appear to be authentic, because they typically include details such as your IP address (numbers that identify your device and its approximate geographical location) and a familiar icon of the browser you're using. Some of them include voiceovers or annoying alert sounds. Some of them will spawn multiple tabs or windows by the dozens. It might seem there is no way to close the windows or otherwise dismiss the popups. You might not be able to control Safari, and you can't find a way to quit the app. Even if you were to completely shut down and restart your Mac or your iPhone, the annoying popups might just keep reappearing.
The above screenshots are mere examples. There are thousands of variations of this scam whose exact appearance and wording can take any form. There are also millions of permutations of the 'toll-free' phone numbers they provide, and they can easily originate from the other side of the globe. These scams are easily created, simple to distribute, and new examples appear every day.
A variant of the same scam will cause a webpage to appear accusing you of engaging in some sordid or illegal Internet activity. The page might bear official-looking government or law enforcement seals, say your Mac is infected with some ick, and / or employ technobabble intended either to intimidate you or create an impression of authenticity.
- Needless to say whatever text they contain should be utterly disregarded, because it's all false: Your Mac is not infected with anything and you did nothing wrong. What you're experiencing is a lame and 100% fraudulent attempt to extort money from you. No matter how legitimate the message appears to be, it did not originate with Apple, the FBI, the IRS, RCMP, Bundespolizei or any legitimate organization.
- If you closely examine the page you might find a 'disclaimer' written in very tiny text, containing what may be the only accurate information on it. The exact text extracted verbatim from one of the above scam examples follows: 'The webpage and pop-up is only for advertisement use. In no way claiming to be Microsoft and claiming a definite error has occurred. The webpage does not take any personal or critical information. The webpage owners are not held liable for any actions taken on your system by third parties. Call at your own free will.' Who could object to that? That's about as sincere as it gets.
- These scams are routinely perpetrated by criminals around the world in an effort to convince you into giving them money. They cannot succeed without your active participation. Don't be a victim.
When you can't find a way around this problem—when you can't close the page or even quit the web browser you're using—it might seem that you're stuck and there is no way out. If that describes your situation, read on.
- Whatever you do, never call any phone numbers that appear. They will just want payment, usually in multiple hundreds of US dollars. Worse yet, they may attempt to deceive you into granting them remote control of your Mac, conceivably enabling them to install a 'backdoor' granting criminals unfettered ability to harvest any or all the information contained on your Mac, to be used for any conceivable purpose. That's a road you do not want to travel. Never allow anyone to remotely log in to and use a Mac that you own and control.
- If you already called, read the Appendix.
There are different solutions for Safari on the Mac and Safari on an iPhone or iPad device. Follow the applicable one below. Although the instructions specifically address Safari, they are easily adapted to other web browsers.
Solution (Mac):
Some of these scam popup messages are very easy to dismiss:
- If a checkbox appears with the text 'Don't show more alerts from this webpage', select it, then click the Leave Page or OK button.
- If that option does not appear, try repeatedly and quickly clicking the Leave Page or OK button while also pressing the key combination ⌘ W.
If the Leave Page or OK button is not visible because the dialog box extends beyond your display's lower limit, the Return or Enter key should perform the equivalent action.
Either option may result in interrupting the script preventing you from closing the page normally. If it does, you're finished. If not, or you grow tired of that method, continue below.
- Quit Safari. If necessary, force Safari to close by following these instructions: Force an app to close on your Mac - Apple Support.
- Summary: choose (Apple menu) > Force Quit...
- Or, using three fingers press the three-key chord ⌘ (the Command key, next to the space bar) Option (the key next to it) Escape (the key at the upper left of your keyboard or Touch Bar).
- A dialog box with the title Force Quit Applications will open.
- Choose Safari, click the Force Quit button, and confirm the dialog with Force Quit again.
- Close the dialog box.
- Press and hold a Shift key and keep it depressed while launching Safari again.
- When Safari opens, release the Shift key.
- This action prevents Safari's previously loaded pages from loading again upon launch.
If that does not immediately fix the problem:
- Force Safari to quit again.
- Disconnect from the Internet by selecting Wi-Fi 'off' in the Mac's menu bar, or disconnecting its Ethernet cable if you're not using wireless. See pictures below.
| Turn Wi-Fi 'off' | Disconnect Ethernet cable (MacBook Pro) | Disconnect Ethernet cable (iMac) |
System Log Mac Hacked
- Launch Safari again by pressing and holding a Shift key while launching Safari.
No pages will be able to load since you're not connected to the Internet.
- Select the Safari menu > Preferences > General, and review your home page selection.
- Select the Privacy pane > Remove All Website Data... > Remove Now.
After you reconnect to the Internet, you will need to sign in again with all websites that require authentication (such as this one).
- Close the Preferences window.
- (optional) Select the History menu > Clear History...
Choose an appropriate period to clear from the dropdown menu. That action will ensure you don't inadvertently navigate back to the same problematic web page.
- Turn Wi-Fi back on again or reconnect your Ethernet cable.
You'll be back in business.
In an abundance of caution, consider the following additional actions. They are not required to eliminate the scam webpage but you should review them to determine certain Safari settings have not been unexpectedly altered.
- Open Safari's Preferences... again and select Extensions. Uninstall any Extensions that you are not certain you require by clicking the Uninstall button.
If you are not sure what to uninstall, uninstall all of them. None are required for normal operation.
- Select the Privacy pane and verify Website tracking is configured the way you expect.
- For macOS versions prior to High Sierra: verify 'Cookies and website data' is configured the way you expect. If you are not certain which choice is appropriate, choose 'Allow from websites I visit'.
- For macOS versions prior to Yosemite the equivalent preference is 'Block cookies and other website data' > From third parties and advertisers.
- Click the Manage Website Data... button.
Read what it says: There is no harm in using the Remove All... button, but websites that require login credentials or otherwise retain custom settings will need to be reset as needed (for example, you'll be logged out of websites that require login credentials).
Solution (iOS):
Force Safari to quit by quickly double-clicking the Home button. On that screen, swipe left or right until you find Safari with a preview of the problematic web page. Swipe that image up and away to terminate it:
| Force Close apps |
The unresponsive Safari page will be gone, but if you were to launch Safari again it might just reappear. To prevent that from occurring, go to Settings and scroll down a bit until you see Safari. Tap Safari, then tap Clear History and Website Data. Confirm the dialog that appears next, and you'll be back in business. The effect of clearing website data will require you to 'sign in' again to websites that require authentication (such as this one).
Appendix
What happens when you call the phone number to 'fix' your Mac, PC, or mobile device

This is what happens.
- There might be noise as though lots of people are talking in the background.
That never happens when you call Apple.
- The person who answers may be difficult to understand due to an inability to converse in your native language without a heavy accent.
Legitimate Apple and Microsoft representatives are chosen for their ability to listen to your concerns and to communicate clearly and effectively in your language.
- They will offer to help you fix what's wrong, without asking for payment in advance.
If Apple or Microsoft intends to charge you for their services, they will let you know in advance.
- If you ask who they represent or where they're from, they'll say Apple, or Microsoft, or Google, or some other organization with an impression of legitimacy. It doesn't matter. They're lying.
- They will ask you to connect to some website on your browser. Doesn't matter which browser. Perhaps they will have you type some numbers into the browser's URL field.
That action will load a website providing a download link to legitimate and free software that will enable them to connect to your Mac.
- When the download finishes, you will be asked to install that software, which may require your login credentials.
That dialog box should always be taken seriously. Never provide your login or Apple ID credentials unless you are certain who's asking and know the reason they are required.
- That software will enable a remote user to manipulate your Mac as though they were you sitting right in front of it, including the ability to download and install even more software that can conceivably be used for any imaginable purpose whatsoever—including harvesting your personal information, stealing passwords, mining cryptocurrencies, remotely monitoring your Internet activity, using your device's built-in cameras or microphones to take pictures of you and your surroundings... the possibilities are endless.
- Using the built-in tools on your Mac or PC, the criminals will show you phony 'evidence' of viruses or malware or spyware or unauthorized intrusion, which will rely upon deception to convince you something is horribly wrong.
- It's hard to resist because they're showing you your own Mac, right before your very eyes.
- Remember... they're lying.
- The criminals will reinforce how wise it was of you to call them before any additional damage occurred. You should be so happy you called them. Etcetera.
- They will offer to provide you—perhaps free of charge, perhaps not—some 'cleaning' or 'anti-virus' junk—legitimate commercial software that nevertheless is 100% garbage that should never be installed on any Mac.
That junk is certain to cause even more headaches in the future, for which you'll want to call them again... except the number you called won't work any more.
- For that service they'll offer to provide a subscription-based service normally priced at several hundred dollars but marked down 'today only' to a mere $200 or whatever they can get, based on the naïveté they perceive from you and your apparent willingness to pay.
Pause here to reflect:
- By agreeing to call them and granting permission to access your Mac, the criminals installed legitimate remote access software that can be in turn used to install something illegitimate or nefarious on your Mac, now or at any time in the future.
- Maybe they also got you to pay $20 or more for some 'anti-virus' junk that's normally given away for nothing, because it also exists to harvest your personal information and sell it.
- Maybe you already provided your credit card number and CVV code or even your bank account information, enabling them to rack up huge charges on your credit or debit card now or in the future.
- Maybe you already gave them your Apple ID and its password, enabling them to purchase a limitless amount of Apple products and services.
Or, they'll just sell your Apple ID to like-minded criminals and take the cash up front.
- Now, they want you to buy a subscription service for continued 24/7/365 tech support which you're going to need, because the junk they installed on your Mac is going to make it sick.
- If you decide to back out of their generous offer, they may just lock you out of your Mac—using the very software you just agreed to install.
- To summarize: you willingly allowed criminals to infect your Mac and maybe even paid them to do it.
A profitable day for bad guys who probably reside on the other side of the globe. For you... not so much.
What to do if you were scammed
You fell for the scam. Now what?
- Don't panic:
- Don't be embarrassed either. You're neither the first nor the last person on Earth to become a victim of a scam, and they're only becoming more sophisticated.
- Your task is now to limit and contain whatever damage has already resulted, and to prevent its reoccurrence.
- Disconnect the affected device from the Internet: Turn its Wi-Fi 'off' and disconnect its Ethernet cable if it's connected. See the screenshots above.
- Only after that should you turn the affected Mac or PC completely off:
- Don't just put it to sleep. Shut it down completely. Force it to shut down if you must.
- Do not use it until the breach has been resolved to your satisfaction.
- Using a different device, contact Apple, or Microsoft, as appropriate, or the applicable legitimate providers of the affected devices and services.
- Use the contact information provided on their own secure web pages.
Most of the links returned by popular search engine results are for even more scams.
- You may need Apple's help if you think your Apple ID has been compromised.
- You might need to pay Apple to help you recover. Then again you might not. If you do, it's well worth the $29 they will charge.
- Use the contact information provided on their own secure web pages.
- Contact your bank or credit card issuers and inform them of the breach:
You might need to cancel your credit or debit card or freeze your bank account, depending on if or how you paid.
- If you have a Mac and use Time Machine: confirm your Mac remains disconnected from the Internet, boot macOS Recovery, and restore its content from a Time Machine backup preceding the intrusive event. To learn how to do that read How to use Time Machine to back up or restore your Mac - Apple Support.
If you don't use Time Machine, start using it. It's already incorporated in macOS.
- If you have no backup from which you can completely restore your Mac or PC to a state prior to the intrusive event, you should probably settle for nothing less than completely erasing it and rebuilding it from the ground up—by installing its operating system and software from original sources known to be reliable.
- There are no tools or products that can reliably confirm the total absence of malware. None. Don't bother looking for one.
- Nothing like that exists because it is not logically possible to provide absolute assurance of the absence of all potentially malicious or intrusive software. There are only ways of determining their presence (and which could serve as a decoy for something more difficult to find or eradicate).
- Consider using Apple's two-factor authentication for your Apple ID:
- That slams the door on anyone attempting to use your Apple ID credentials from a device that is not also in your physical possession.
- For services other than Apple's, consider using their functional equivalents.
- Consider contacting an appropriate law enforcement agency:
- They are not likely to be interested in a crime arising beyond their jurisdiction, but are likely to be interested in disseminating information toward preventing this type of criminal activity.
- Links to the US FBI's Internet Crime Complaint Center can be found in the References section below.
- Learn from your experience, and help others learn from it too:
- Give this User Tip to your friends and family. Print it, post it on bulletin boards, shout it from the rooftops, whatever it takes to shut down the bad guys.
- Education is the only effective defense against these and other scams.
- Launch Safari again by pressing and holding a Shift key while launching Safari.
No pages will be able to load since you're not connected to the Internet.
- Select the Safari menu > Preferences > General, and review your home page selection.
- Select the Privacy pane > Remove All Website Data... > Remove Now.
After you reconnect to the Internet, you will need to sign in again with all websites that require authentication (such as this one).
- Close the Preferences window.
- (optional) Select the History menu > Clear History...
Choose an appropriate period to clear from the dropdown menu. That action will ensure you don't inadvertently navigate back to the same problematic web page.
- Turn Wi-Fi back on again or reconnect your Ethernet cable.
You'll be back in business.
In an abundance of caution, consider the following additional actions. They are not required to eliminate the scam webpage but you should review them to determine certain Safari settings have not been unexpectedly altered.
- Open Safari's Preferences... again and select Extensions. Uninstall any Extensions that you are not certain you require by clicking the Uninstall button.
If you are not sure what to uninstall, uninstall all of them. None are required for normal operation.
- Select the Privacy pane and verify Website tracking is configured the way you expect.
- For macOS versions prior to High Sierra: verify 'Cookies and website data' is configured the way you expect. If you are not certain which choice is appropriate, choose 'Allow from websites I visit'.
- For macOS versions prior to Yosemite the equivalent preference is 'Block cookies and other website data' > From third parties and advertisers.
- Click the Manage Website Data... button.
Read what it says: There is no harm in using the Remove All... button, but websites that require login credentials or otherwise retain custom settings will need to be reset as needed (for example, you'll be logged out of websites that require login credentials).
Solution (iOS):
Force Safari to quit by quickly double-clicking the Home button. On that screen, swipe left or right until you find Safari with a preview of the problematic web page. Swipe that image up and away to terminate it:
| Force Close apps |
The unresponsive Safari page will be gone, but if you were to launch Safari again it might just reappear. To prevent that from occurring, go to Settings and scroll down a bit until you see Safari. Tap Safari, then tap Clear History and Website Data. Confirm the dialog that appears next, and you'll be back in business. The effect of clearing website data will require you to 'sign in' again to websites that require authentication (such as this one).
Appendix
What happens when you call the phone number to 'fix' your Mac, PC, or mobile device
This is what happens.
- There might be noise as though lots of people are talking in the background.
That never happens when you call Apple.
- The person who answers may be difficult to understand due to an inability to converse in your native language without a heavy accent.
Legitimate Apple and Microsoft representatives are chosen for their ability to listen to your concerns and to communicate clearly and effectively in your language.
- They will offer to help you fix what's wrong, without asking for payment in advance.
If Apple or Microsoft intends to charge you for their services, they will let you know in advance.
- If you ask who they represent or where they're from, they'll say Apple, or Microsoft, or Google, or some other organization with an impression of legitimacy. It doesn't matter. They're lying.
- They will ask you to connect to some website on your browser. Doesn't matter which browser. Perhaps they will have you type some numbers into the browser's URL field.
That action will load a website providing a download link to legitimate and free software that will enable them to connect to your Mac.
- When the download finishes, you will be asked to install that software, which may require your login credentials.
That dialog box should always be taken seriously. Never provide your login or Apple ID credentials unless you are certain who's asking and know the reason they are required.
- That software will enable a remote user to manipulate your Mac as though they were you sitting right in front of it, including the ability to download and install even more software that can conceivably be used for any imaginable purpose whatsoever—including harvesting your personal information, stealing passwords, mining cryptocurrencies, remotely monitoring your Internet activity, using your device's built-in cameras or microphones to take pictures of you and your surroundings... the possibilities are endless.
- Using the built-in tools on your Mac or PC, the criminals will show you phony 'evidence' of viruses or malware or spyware or unauthorized intrusion, which will rely upon deception to convince you something is horribly wrong.
- It's hard to resist because they're showing you your own Mac, right before your very eyes.
- Remember... they're lying.
- The criminals will reinforce how wise it was of you to call them before any additional damage occurred. You should be so happy you called them. Etcetera.
- They will offer to provide you—perhaps free of charge, perhaps not—some 'cleaning' or 'anti-virus' junk—legitimate commercial software that nevertheless is 100% garbage that should never be installed on any Mac.
That junk is certain to cause even more headaches in the future, for which you'll want to call them again... except the number you called won't work any more.
- For that service they'll offer to provide a subscription-based service normally priced at several hundred dollars but marked down 'today only' to a mere $200 or whatever they can get, based on the naïveté they perceive from you and your apparent willingness to pay.
Pause here to reflect:
- By agreeing to call them and granting permission to access your Mac, the criminals installed legitimate remote access software that can be in turn used to install something illegitimate or nefarious on your Mac, now or at any time in the future.
- Maybe they also got you to pay $20 or more for some 'anti-virus' junk that's normally given away for nothing, because it also exists to harvest your personal information and sell it.
- Maybe you already provided your credit card number and CVV code or even your bank account information, enabling them to rack up huge charges on your credit or debit card now or in the future.
- Maybe you already gave them your Apple ID and its password, enabling them to purchase a limitless amount of Apple products and services.
Or, they'll just sell your Apple ID to like-minded criminals and take the cash up front.
- Now, they want you to buy a subscription service for continued 24/7/365 tech support which you're going to need, because the junk they installed on your Mac is going to make it sick.
- If you decide to back out of their generous offer, they may just lock you out of your Mac—using the very software you just agreed to install.
- To summarize: you willingly allowed criminals to infect your Mac and maybe even paid them to do it.
A profitable day for bad guys who probably reside on the other side of the globe. For you... not so much.
What to do if you were scammed
You fell for the scam. Now what?
- Don't panic:
- Don't be embarrassed either. You're neither the first nor the last person on Earth to become a victim of a scam, and they're only becoming more sophisticated.
- Your task is now to limit and contain whatever damage has already resulted, and to prevent its reoccurrence.
- Disconnect the affected device from the Internet: Turn its Wi-Fi 'off' and disconnect its Ethernet cable if it's connected. See the screenshots above.
- Only after that should you turn the affected Mac or PC completely off:
- Don't just put it to sleep. Shut it down completely. Force it to shut down if you must.
- Do not use it until the breach has been resolved to your satisfaction.
- Using a different device, contact Apple, or Microsoft, as appropriate, or the applicable legitimate providers of the affected devices and services.
- Use the contact information provided on their own secure web pages.
Most of the links returned by popular search engine results are for even more scams.
- You may need Apple's help if you think your Apple ID has been compromised.
- You might need to pay Apple to help you recover. Then again you might not. If you do, it's well worth the $29 they will charge.
- Use the contact information provided on their own secure web pages.
- Contact your bank or credit card issuers and inform them of the breach:
You might need to cancel your credit or debit card or freeze your bank account, depending on if or how you paid.
- If you have a Mac and use Time Machine: confirm your Mac remains disconnected from the Internet, boot macOS Recovery, and restore its content from a Time Machine backup preceding the intrusive event. To learn how to do that read How to use Time Machine to back up or restore your Mac - Apple Support.
If you don't use Time Machine, start using it. It's already incorporated in macOS.
- If you have no backup from which you can completely restore your Mac or PC to a state prior to the intrusive event, you should probably settle for nothing less than completely erasing it and rebuilding it from the ground up—by installing its operating system and software from original sources known to be reliable.
- There are no tools or products that can reliably confirm the total absence of malware. None. Don't bother looking for one.
- Nothing like that exists because it is not logically possible to provide absolute assurance of the absence of all potentially malicious or intrusive software. There are only ways of determining their presence (and which could serve as a decoy for something more difficult to find or eradicate).
- Consider using Apple's two-factor authentication for your Apple ID:
- That slams the door on anyone attempting to use your Apple ID credentials from a device that is not also in your physical possession.
- For services other than Apple's, consider using their functional equivalents.
- Consider contacting an appropriate law enforcement agency:
- They are not likely to be interested in a crime arising beyond their jurisdiction, but are likely to be interested in disseminating information toward preventing this type of criminal activity.
- Links to the US FBI's Internet Crime Complaint Center can be found in the References section below.
- Learn from your experience, and help others learn from it too:
- Give this User Tip to your friends and family. Print it, post it on bulletin boards, shout it from the rooftops, whatever it takes to shut down the bad guys.
- Education is the only effective defense against these and other scams.
References and other resources:
FBI statement: http://www.fbi.gov/news/stories/2012/august/new-internet-scam
System Log Mac Hacked Download
FTC statement: https://www.consumer.ftc.gov/articles/0076-phone-scams
IRS statement: https://www.irs.gov/uac/irs-urges-public-to-stay-alert-for-scam-phone-calls
Microsoft: http://www.microsoft.com/security/portal/mmpc/shared/ransomware.aspx
System Log Mac Hacked 2
Moneypak: https://www.moneypak.com/ProtectYourMoney.aspx#
System Log Mac Hacked Client Windows
Related articles: How to install adware
